new default branch is main
This commit is contained in:
parent
b60b083af8
commit
33388217a5
|
|
@ -4,13 +4,13 @@ Addons are scripts that analyses Cppcheck dump files to check compatibility with
|
|||
|
||||
## Supported addons
|
||||
|
||||
+ [cert.py](https://github.com/danmar/cppcheck/blob/master/addons/cert.py)
|
||||
+ [cert.py](https://github.com/danmar/cppcheck/blob/main/addons/cert.py)
|
||||
Checks for compliance with the safe programming standard [CERT](http://www.cert.org/secure-coding/).
|
||||
+ [misra.py](https://github.com/danmar/cppcheck/blob/master/addons/misra.py)
|
||||
Used to verify compliance with MISRA C 2012 - a proprietary set of guidelines to avoid such questionable code, developed for embedded systems. Since this standard is proprietary, cppcheck does not display error text by specifying only the number of violated rules (for example, [c2012-21.3]). If you want to display full texts for violated rules, you will need to create a text file containing MISRA rules, which you will have to pass when calling the script with `--rule-texts` key. Some examples of rule texts files available in [tests directory](https://github.com/danmar/cppcheck/blob/master/addons/test/misra/).
|
||||
+ [y2038.py](https://github.com/danmar/cppcheck/blob/master/addons/y2038.py)
|
||||
Checks Linux system for [year 2038 problem](https://en.wikipedia.org/wiki/Year_2038_problem) safety. This required [modified environment](https://github.com/3adev/y2038). See complete description [here](https://github.com/danmar/cppcheck/blob/master/addons/doc/y2038.txt).
|
||||
+ [threadsafety.py](https://github.com/danmar/cppcheck/blob/master/addons/threadsafety.py)
|
||||
+ [misra.py](https://github.com/danmar/cppcheck/blob/main/addons/misra.py)
|
||||
Used to verify compliance with MISRA C 2012 - a proprietary set of guidelines to avoid such questionable code, developed for embedded systems. Since this standard is proprietary, cppcheck does not display error text by specifying only the number of violated rules (for example, [c2012-21.3]). If you want to display full texts for violated rules, you will need to create a text file containing MISRA rules, which you will have to pass when calling the script with `--rule-texts` key. Some examples of rule texts files available in [tests directory](https://github.com/danmar/cppcheck/blob/main/addons/test/misra/).
|
||||
+ [y2038.py](https://github.com/danmar/cppcheck/blob/main/addons/y2038.py)
|
||||
Checks Linux system for [year 2038 problem](https://en.wikipedia.org/wiki/Year_2038_problem) safety. This required [modified environment](https://github.com/3adev/y2038). See complete description [here](https://github.com/danmar/cppcheck/blob/main/addons/doc/y2038.txt).
|
||||
+ [threadsafety.py](https://github.com/danmar/cppcheck/blob/main/addons/threadsafety.py)
|
||||
Analyse Cppcheck dump files to locate threadsafety issues like static local objects used by multiple threads.
|
||||
|
||||
## Usage
|
||||
|
|
@ -34,5 +34,5 @@ This allows you to add additional parameters when calling the script (for exampl
|
|||
|
||||
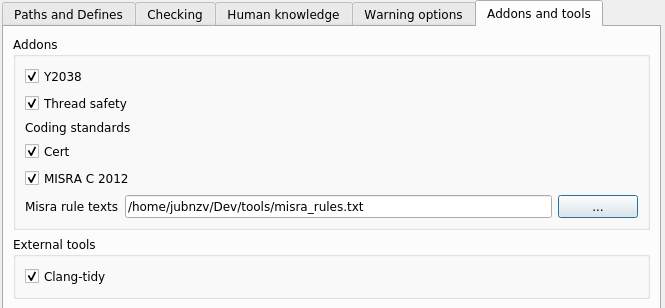
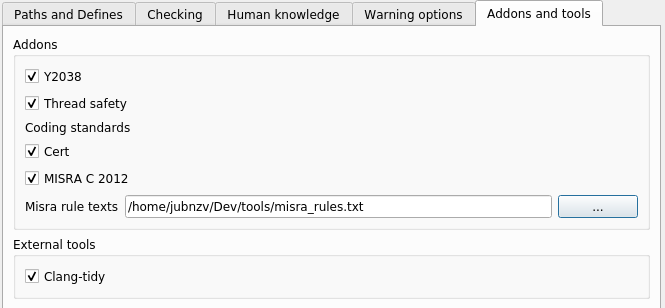
When using the graphical interface `cppcheck-gui`, the selection and configuration of addons is carried out on the tab `Addons and tools` in the project settings (`Edit Project File`):
|
||||
|
||||
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -722,23 +722,23 @@ Cppcheck is distributed with a few addons which are listed below.
|
|||
|
||||
### cert.py
|
||||
|
||||
[cert.py](https://github.com/danmar/cppcheck/blob/master/addons/cert.py) checks for compliance with the safe programming standard [SEI CERT](http://www.cert.org/secure-coding/).
|
||||
[cert.py](https://github.com/danmar/cppcheck/blob/main/addons/cert.py) checks for compliance with the safe programming standard [SEI CERT](http://www.cert.org/secure-coding/).
|
||||
|
||||
### misra.py
|
||||
|
||||
[misra.py](https://github.com/danmar/cppcheck/blob/master/addons/misra.py) is used to verify compliance with MISRA C 2012 - a proprietary set of guidelines to avoid such questionable code, developed for embedded systems.
|
||||
[misra.py](https://github.com/danmar/cppcheck/blob/main/addons/misra.py) is used to verify compliance with MISRA C 2012 - a proprietary set of guidelines to avoid such questionable code, developed for embedded systems.
|
||||
|
||||
Since this standard is proprietary, cppcheck does not display error text by specifying only the number of violated rules (for example, [c2012-21.3]). If you want to display full texts for violated rules, you will need to create a text file containing MISRA rules, which you will have to pass when calling the script with `--rule-texts` key. Some examples of rule texts files available in [tests directory](https://github.com/danmar/cppcheck/blob/master/addons/test/misra/).
|
||||
Since this standard is proprietary, cppcheck does not display error text by specifying only the number of violated rules (for example, [c2012-21.3]). If you want to display full texts for violated rules, you will need to create a text file containing MISRA rules, which you will have to pass when calling the script with `--rule-texts` key. Some examples of rule texts files available in [tests directory](https://github.com/danmar/cppcheck/blob/main/addons/test/misra/).
|
||||
|
||||
You can also suppress some unwanted rules using `--suppress-rules` option. Suppressed rules should be set as comma-separated listed, for example: `--suppress-rules 21.1,18.7`. The full list of supported rules is available on [Cppcheck](http://cppcheck.sourceforge.net/misra.php) home page.
|
||||
|
||||
### y2038.py
|
||||
|
||||
[y2038.py](https://github.com/danmar/cppcheck/blob/master/addons/y2038.py) checks Linux system for [year 2038 problem](https://en.wikipedia.org/wiki/Year_2038_problem) safety. This required [modified environment](https://github.com/3adev/y2038). See complete description [here](https://github.com/danmar/cppcheck/blob/master/addons/doc/y2038.txt).
|
||||
[y2038.py](https://github.com/danmar/cppcheck/blob/main/addons/y2038.py) checks Linux system for [year 2038 problem](https://en.wikipedia.org/wiki/Year_2038_problem) safety. This required [modified environment](https://github.com/3adev/y2038). See complete description [here](https://github.com/danmar/cppcheck/blob/main/addons/doc/y2038.txt).
|
||||
|
||||
### threadsafety.py
|
||||
|
||||
[threadsafety.py](https://github.com/danmar/cppcheck/blob/master/addons/threadsafety.py) analyse Cppcheck dump files to locate thread safety issues like static local objects used by multiple threads.
|
||||
[threadsafety.py](https://github.com/danmar/cppcheck/blob/main/addons/threadsafety.py) analyse Cppcheck dump files to locate thread safety issues like static local objects used by multiple threads.
|
||||
|
||||
## Running Addons
|
||||
|
||||
|
|
|
|||
|
|
@ -2,7 +2,7 @@
|
|||
|
||||
|GitHub Actions|Linux Build Status|Windows Build Status|OSS-Fuzz|Coverity Scan Build Status|License|
|
||||
|:-:|:--:|:--:|:--:|:--:|:-:|
|
||||
|[](https://github.com/danmar/cppcheck/actions?query=workflow%3ACI)|[](https://travis-ci.org/danmar/cppcheck)|[](https://ci.appveyor.com/project/danmar/cppcheck/branch/master)|[](https://bugs.chromium.org/p/oss-fuzz/issues/list?sort=-opened&can=1&q=proj:cppcheck)|[](https://scan.coverity.com/projects/512)|[](https://opensource.org/licenses/GPL-3.0)
|
||||
|[](https://github.com/danmar/cppcheck/actions?query=workflow%3ACI)|[](https://travis-ci.org/danmar/cppcheck)|[](https://ci.appveyor.com/project/danmar/cppcheck/branch/main)|[](https://bugs.chromium.org/p/oss-fuzz/issues/list?sort=-opened&can=1&q=proj:cppcheck)|[](https://scan.coverity.com/projects/512)|[](https://opensource.org/licenses/GPL-3.0)
|
||||
|
||||
## About the name
|
||||
|
||||
|
|
|
|||
|
|
@ -85,7 +85,7 @@ Script to donate CPU time to Cppcheck project by checking current Debian package
|
|||
|
||||
### * tools/test-my-pr.py
|
||||
|
||||
Script to compare result of working Cppcheck from your branch with master branch.
|
||||
Script to compare result of working Cppcheck from your branch with main branch.
|
||||
|
||||
### * tools/triage
|
||||
|
||||
|
|
|
|||
|
|
@ -1,7 +1,7 @@
|
|||
#!/usr/bin/env python3
|
||||
|
||||
# Run this script from your branch with proposed Cppcheck patch to verify your
|
||||
# patch against current master. It will compare output of testing a bunch of
|
||||
# patch against current main. It will compare output of testing a bunch of
|
||||
# opensource packages
|
||||
|
||||
import donate_cpu_lib as lib
|
||||
|
|
@ -19,7 +19,7 @@ def format_float(a, b=1):
|
|||
|
||||
|
||||
if __name__ == "__main__":
|
||||
parser = argparse.ArgumentParser(description='Run this script from your branch with proposed Cppcheck patch to verify your patch against current master. It will compare output of testing bunch of opensource packages')
|
||||
parser = argparse.ArgumentParser(description='Run this script from your branch with proposed Cppcheck patch to verify your patch against current main. It will compare output of testing bunch of opensource packages')
|
||||
parser.add_argument('-j', default=1, type=int, help='Concurency execution threads')
|
||||
parser.add_argument('-p', default=256, type=int, help='Count of packages to check')
|
||||
parser.add_argument('-o', default='my_check_diff.log', help='Filename of result inside a working path dir')
|
||||
|
|
@ -31,7 +31,7 @@ if __name__ == "__main__":
|
|||
work_path = os.path.abspath(args.work_path)
|
||||
if not os.path.exists(work_path):
|
||||
os.makedirs(work_path)
|
||||
master_dir = os.path.join(work_path, 'cppcheck')
|
||||
main_dir = os.path.join(work_path, 'cppcheck')
|
||||
|
||||
jobs = '-j' + str(args.j)
|
||||
result_file = os.path.join(work_path, args.o)
|
||||
|
|
@ -44,29 +44,29 @@ if __name__ == "__main__":
|
|||
if os.path.exists(timing_file):
|
||||
os.remove(timing_file)
|
||||
|
||||
if not lib.get_cppcheck(master_dir, work_path):
|
||||
print('Failed to clone master of Cppcheck, retry later')
|
||||
if not lib.get_cppcheck(main_dir, work_path):
|
||||
print('Failed to clone main of Cppcheck, retry later')
|
||||
sys.exit(1)
|
||||
|
||||
try:
|
||||
os.chdir(your_repo_dir)
|
||||
commit_id = (subprocess.check_output(['git', 'merge-base', 'origin/master', 'HEAD'])).strip().decode('ascii')
|
||||
commit_id = (subprocess.check_output(['git', 'merge-base', 'origin/main', 'HEAD'])).strip().decode('ascii')
|
||||
with open(result_file, 'a') as myfile:
|
||||
myfile.write('Common ancestor: ' + commit_id + '\n\n')
|
||||
package_width = '140'
|
||||
timing_width = '>7'
|
||||
with open(timing_file, 'a') as myfile:
|
||||
myfile.write('{:{package_width}} {:{timing_width}} {:{timing_width}} {:{timing_width}}\n'.format(
|
||||
'Package', 'master', 'your', 'Factor', package_width=package_width, timing_width=timing_width))
|
||||
'Package', 'main', 'your', 'Factor', package_width=package_width, timing_width=timing_width))
|
||||
|
||||
os.chdir(master_dir)
|
||||
os.chdir(main_dir)
|
||||
subprocess.check_call(['git', 'checkout', '-f', commit_id])
|
||||
except:
|
||||
print('Failed to switch to common ancestor of your branch and master')
|
||||
print('Failed to switch to common ancestor of your branch and main')
|
||||
sys.exit(1)
|
||||
|
||||
if not lib.compile_cppcheck(master_dir, jobs):
|
||||
print('Failed to compile master of Cppcheck')
|
||||
if not lib.compile_cppcheck(main_dir, jobs):
|
||||
print('Failed to compile main of Cppcheck')
|
||||
sys.exit(1)
|
||||
|
||||
print('Testing your PR from directory: ' + your_repo_dir)
|
||||
|
|
@ -100,24 +100,24 @@ if __name__ == "__main__":
|
|||
|
||||
results_to_diff = []
|
||||
|
||||
master_crashed = False
|
||||
main_crashed = False
|
||||
your_crashed = False
|
||||
|
||||
master_timeout = False
|
||||
main_timeout = False
|
||||
your_timeout = False
|
||||
|
||||
libraries = lib.get_libraries()
|
||||
c, errout, info, time_master, cppcheck_options, timing_info = lib.scan_package(work_path, master_dir, jobs, libraries)
|
||||
c, errout, info, time_main, cppcheck_options, timing_info = lib.scan_package(work_path, main_dir, jobs, libraries)
|
||||
if c < 0:
|
||||
if c == -101 and 'error: could not find or open any of the paths given.' in errout:
|
||||
# No sourcefile found (for example only headers present)
|
||||
print('Error: 101')
|
||||
elif c == lib.RETURN_CODE_TIMEOUT:
|
||||
print('Master timed out!')
|
||||
master_timeout = True
|
||||
print('Main timed out!')
|
||||
main_timeout = True
|
||||
else:
|
||||
print('Master crashed!')
|
||||
master_crashed = True
|
||||
print('Main crashed!')
|
||||
main_crashed = True
|
||||
results_to_diff.append(errout)
|
||||
|
||||
c, errout, info, time_your, cppcheck_options, timing_info = lib.scan_package(work_path, your_repo_dir, jobs, libraries)
|
||||
|
|
@ -133,36 +133,36 @@ if __name__ == "__main__":
|
|||
your_crashed = True
|
||||
results_to_diff.append(errout)
|
||||
|
||||
if master_crashed or your_crashed:
|
||||
if main_crashed or your_crashed:
|
||||
who = None
|
||||
if master_crashed and your_crashed:
|
||||
if main_crashed and your_crashed:
|
||||
who = 'Both'
|
||||
elif master_crashed:
|
||||
who = 'Master'
|
||||
elif main_crashed:
|
||||
who = 'Main'
|
||||
else:
|
||||
who = 'Your'
|
||||
crashes.append(package + ' ' + who)
|
||||
|
||||
if master_timeout or your_timeout:
|
||||
if main_timeout or your_timeout:
|
||||
who = None
|
||||
if master_timeout and your_timeout:
|
||||
if main_timeout and your_timeout:
|
||||
who = 'Both'
|
||||
elif master_timeout:
|
||||
who = 'Master'
|
||||
elif main_timeout:
|
||||
who = 'Main'
|
||||
else:
|
||||
who = 'Your'
|
||||
timeouts.append(package + ' ' + who)
|
||||
|
||||
with open(result_file, 'a') as myfile:
|
||||
myfile.write(package + '\n')
|
||||
diff = lib.diff_results(work_path, 'master', results_to_diff[0], 'your', results_to_diff[1])
|
||||
diff = lib.diff_results(work_path, 'main', results_to_diff[0], 'your', results_to_diff[1])
|
||||
if diff != '':
|
||||
myfile.write('diff:\n' + diff + '\n')
|
||||
|
||||
with open(timing_file, 'a') as myfile:
|
||||
myfile.write('{:{package_width}} {:{timing_width}} {:{timing_width}} {:{timing_width}}\n'.format(
|
||||
package, format_float(time_master),
|
||||
format_float(time_your), format_float(time_your, time_master),
|
||||
package, format_float(time_main),
|
||||
format_float(time_your), format_float(time_your, time_main),
|
||||
package_width=package_width, timing_width=timing_width))
|
||||
|
||||
packages_processed += 1
|
||||
|
|
|
|||
|
|
@ -18,6 +18,6 @@ do
|
|||
make clean
|
||||
make -j4 > /dev/null
|
||||
/usr/bin/time -a -o times-tags.txt ./cppcheck sources -q 2> /dev/null
|
||||
git checkout master
|
||||
git checkout main
|
||||
git branch -D "$i"
|
||||
done
|
||||
|
|
|
|||
|
|
@ -20,7 +20,7 @@ const int MAX_ERRORS = 100;
|
|||
MainWindow::MainWindow(QWidget *parent) :
|
||||
QMainWindow(parent),
|
||||
ui(new Ui::MainWindow),
|
||||
mVersionRe("^(master|your|head|1.[0-9][0-9]) (.*)"),
|
||||
mVersionRe("^(master|main|your|head|1.[0-9][0-9]) (.*)"),
|
||||
hFiles{"*.hpp", "*.h", "*.hxx", "*.hh", "*.tpp", "*.txx"},
|
||||
srcFiles{"*.cpp", "*.cxx", "*.cc", "*.c++", "*.C", "*.c", "*.cl"}
|
||||
{
|
||||
|
|
|
|||
Loading…
Reference in New Issue