|
|
||
|---|---|---|
| .. | ||
| doc | ||
| test | ||
| README.md | ||
| ROS_naming.json | ||
| __init__.py | ||
| cppcheck.py | ||
| cppcheckdata.doxyfile | ||
| cppcheckdata.py | ||
| findcasts.py | ||
| misc.py | ||
| misra.py | ||
| misra_9.py | ||
| naming.json | ||
| naming.py | ||
| namingng.py | ||
| runaddon.py | ||
| threadsafety.py | ||
| y2038.py | ||
README.md
Cppcheck addons
Addons are scripts that analyses Cppcheck dump files to check compatibility with secure coding standards and to locate various issues.
Supported addons
- misra.py
Used to verify compliance with MISRA C 2012 - a proprietary set of guidelines to avoid such questionable code, developed for embedded systems. Since this standard is proprietary, cppcheck does not display error text by specifying only the number of violated rules (for example, [c2012-21.3]). If you want to display full texts for violated rules, you will need to create a text file containing MISRA rules, which you will have to pass when calling the script with
--rule-textskey. Some examples of rule texts files available in tests directory. - y2038.py Checks Linux system for year 2038 problem safety. This required modified environment. See complete description here.
- threadsafety.py Analyse Cppcheck dump files to locate threadsafety issues like static local objects used by multiple threads.
- naming.py Enforces naming conventions across the code.
- namingng.py Enforces naming conventions across the code. Enhanced version with support for type prefixes in variable and function names.
- findcasts.py Locates casts in the code.
- misc.py Performs miscellaneous checks.
Other files
- doc Additional files for documentation generation.
- tests Contains various unit tests for the addons.
- cppcheck.py Internal helper used by Cppcheck binary to run the addons.
- cppcheckdata.doxyfile Configuration file for documentation generation.
- cppcheckdata.py Helper class for reading Cppcheck dump files within an addon.
- misra_9.py
Implementation of the MISRA 9.x rules used by
misraaddon. - naming.json
Example configuration for
namingngaddon. - ROS_naming.json
Example configuration for the
namingngaddon enforcing the ROS naming convention for C++ . - runaddon.py Internal helper used by Cppcheck binary to run the addons.
Usage
Command line interface
cppcheck --addon=misc src/test.c
It is also possible to call scripts as follows:
cppcheck --dump --quiet src/test.c
python misc.py src/test.c.dump
python misra.py --rule-texts=~/misra_rules.txt src/test.c.dump
This allows you to add additional parameters when calling the script (for example, --rule-texts for misra.py). The full list of available parameters can be found by calling any script with the --help flag.
GUI
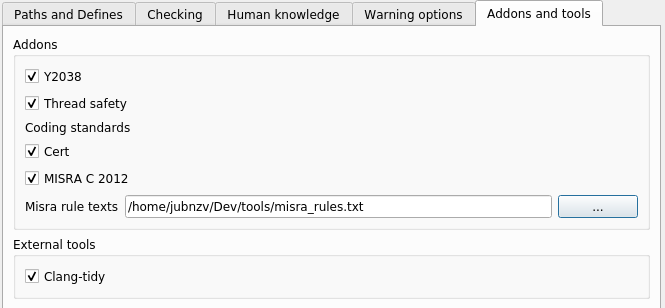
When using the graphical interface cppcheck-gui, the selection and configuration of addons is carried out on the tab Addons and tools in the project settings (Edit Project File):